An Exhaustive Survey on Security Concerns and Solutions at Different Components of Virtualization | Semantic Scholar

Conservative GOP figures use Paul Pelosi attack as election talking point, punchline - The Boston Globe

Chilling moment woman buys Tesco hammer to injure herself and falsely accuse men of rape - Mirror Online
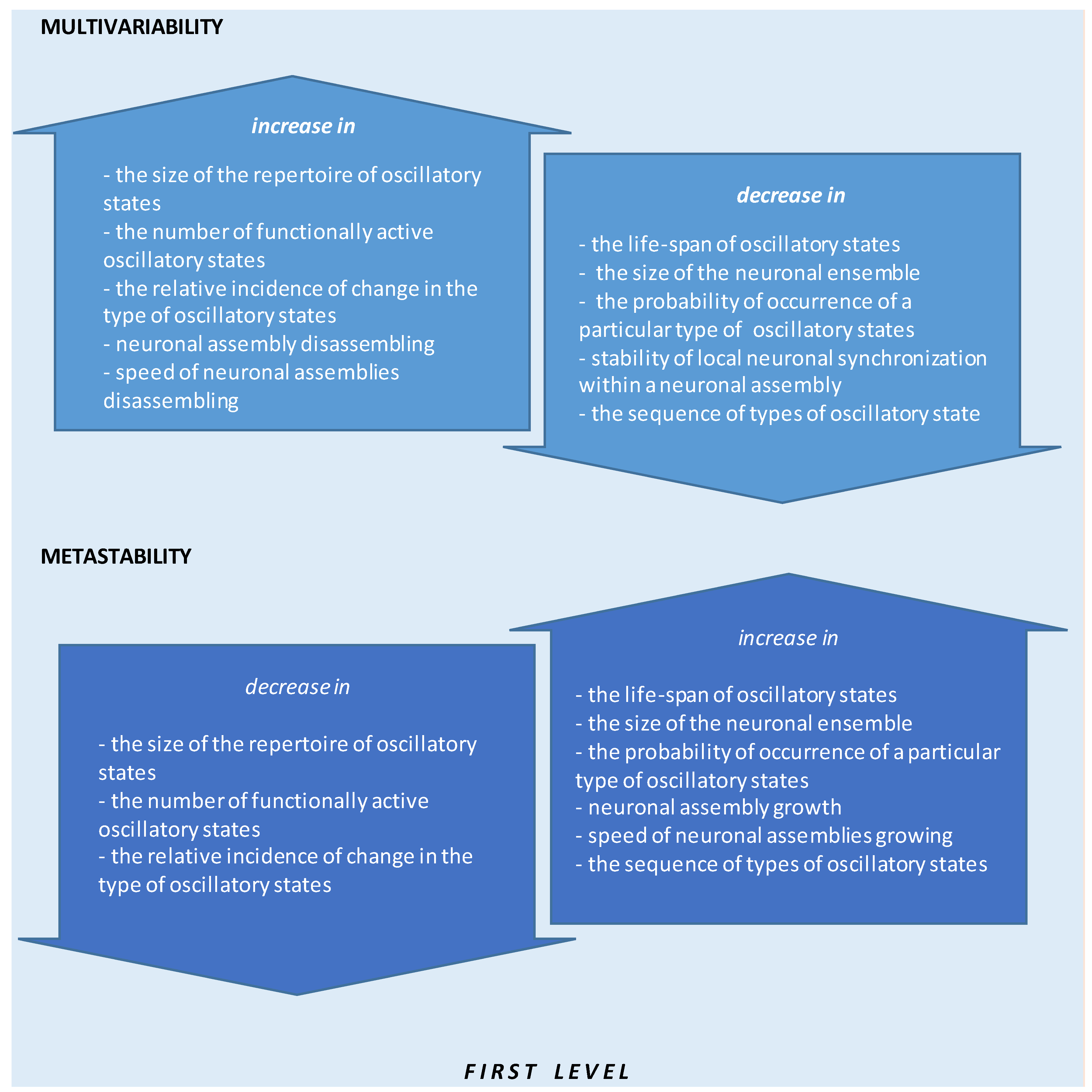
Applied Sciences | Free Full-Text | Quantitative Electroencephalogram (qEEG) as a Natural and Non-Invasive Window into Living Brain and Mind in the Functional Continuum of Healthy and Pathological Conditions













![Amazon.com: Hammer House of Horror: The Complete Series [Blu-ray] : Movies & TV Amazon.com: Hammer House of Horror: The Complete Series [Blu-ray] : Movies & TV](https://m.media-amazon.com/images/I/4181IGHYKRL._AC_UF894,1000_QL80_.jpg)